IMPROVING SECURITY, migrating to the cloud, and increasing IT productivity through automation are the top three priorities for IT professionals at SMBs, according to Kaseya‘s 2021 IT Operations Survey. Other key priorities include delivering higher service levels, reducing IT costs, and supporting business innovation initiatives.
Accordingly, 57% of respondents plan to raise spending on IT security this year, 54% plan to boost spending on cloud infrastructure (public, private, and hybrid), and 42% have upped their budget for IT management tools.
Despite respondents’ eagerness to automate IT tasks, progress toward achieving a high level of IT operational maturity remains slow, the survey finds. More than a quarter of IT teams (27%) are at the lowest level of maturity (Reactive) on a scale of 1-5. The highest percentage (33%) of respondents are at the third level (Proactive), where they’re streamlining IT operations by automating repetitive tasks and remedial actions. Only 14% are at the highest level (Strategic) and play a role in driving business innovation.
The top challenge in 2021, according to 54% of respondents, goes hand in hand with the top priority: cybersecurity/data protection. That is followed by not enough IT budget or resources to meet demands (30%) and legacy systems hampering growth and innovation (24%).
Budgets are getting back on track with pre-pandemic allocations, however, with more than a third of respondents reporting that their IT budget increased in 2021 and 35% saying spending is level with 2020.
Top budget drivers for 2021 include updating IT infrastructure (52%), business growth (49%), and remote workforce management (42%).
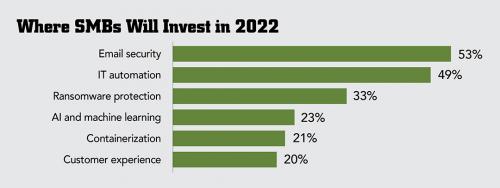
Looking ahead to 2022 budgets, cybersecurity solutions top the list of what IT professionals expect to invest in, with 53% of respondents planning to budget for email security tools like phishing prevention software and 33% investing in ransomware protection. In addition, almost half (49%) plan to invest in IT automation. Take note where your customers plan to spend, channel pros.
Image: iStock