THE COMPLEXITY of cloud security serves as both a challenge and an opportunity for channel pros.
On one hand, the cloud introduces new and sometimes unfamiliar security requirements. Not only does it multiply connection points and overall exposure, it introduces more vendors and additional layers of complexity. Moreover, it’s no longer possible to rely solely on web application firewalls, data loss prevention, secure web gateways, and basic authentication tools. On the other hand, channel pros who guide clients through the maze and help them arrive at more secure IT frameworks can boost trust and, ultimately, achieve deeper relationships based on value.
While securing IT systems and locking down data has never been simple, it’s grown exponentially more complex in the era of cloud computing and widely dispersed systems. Today, data and information flow across devices, offices, and companies. “”It’s a borderless world of data,”” observes John Yeoh, global vice president of research at the Cloud Security Alliance (CSA).
It’s safe to say that the old rules of security don’t apply in the cloud. MPLS networks with fixed providers have fallen by the wayside. Many on-premises tools and applications don’t work well in the cloud, where servers and containers are typically software-based. Names and IP addresses constantly change, and businesses frequently don’t have full control over containers, applications, and more.
“”You’re often subscribing to someone else’s application, and there’s often a greater degree of abstraction because you don’t own the network or the virtual machines,”” says Steve Riley, senior director of research at IT consulting firm Gartner. Given that lack of control, “”it’s necessary to move away from the idea of a secure network of systems and enable a network of secure systems. This means hardening the host or container because that’s what a subscriber has control over,”” Riley says.
In the cloud age, therefore, managed service and IT solution providers need to rethink the way they design cybersecurity solutions. “”Cloud security requires a different mindset and a different framework—and it is evolving rapidly,”” says Joe Vadakkan, global head of cloud security at cybersecurity integration firm Optiv. “”It increasingly requires highly automated and scalable solutions.””
Out of the Haze
The challenges surrounding cloud security are significant. A 2019 study of 700 IT and security professionals conducted by CSA and AlgoSec found that common problems revolve around misconfigurations, visibility into the entire cloud estate, inadequate audit preparation and compliance, holistic management of cloud and on-premises environments, and managing multiple clouds. What’s more, human error factored into many problems. In all, 11.4% of respondents reported a cloud security incident in the past year, and 42.5% had a network or application outage. Eighty-one percent of cloud users said they encountered significant security concerns.
At a most fundamental level, cloud security incorporates any and all data that touches private, public, and hybrid clouds. The risks and protections are similar to conventional IT systems, but the topography and structure of cloud networks create far more intrusion points and data exposure hazards. APIs make it easier to bypass conventional perimeter-based security protections, and in many cases provide a backdoor into systems that can lead to a takedown. Clouds are also highly dynamic, and threats to the infrastructure are constantly changing.
And while cloud providers—including the likes of AWS, Microsoft, Google, Rackspace, and Oracle—have strong security controls in their data centers and offer security tools in applications, default configuration settings can create problems. “”Default configurations aren’t necessarily safe, and the cloud provider may not notify you that this is the case,”” Yeoh explains.
Problems often revolve around authentication methods, permissions, whether data is encrypted at rest and in motion, and which cloud services and components are open by default. Not surprisingly, cloud providers often lean toward convenience and ease of use. Often, channel pros and others engineering and designing IT frameworks don’t bother to examine how systems are configured and how they interact with each other within the realm of security. “”If you’re not careful,”” Yeoh says, “”you inadvertently wind up with systems that can expose a lot of sensitive information. If someone has access to cloud components, folders, or files, they can do a tremendous amount of damage.””
For MSPs, it’s unwise to view cybersecurity as the primary responsibility of cloud service providers. There are simply too many moving parts and bits of data to think that checking settings and connections is sufficient.
“”Unless it’s specifically called out in a contract, a cloud provider’s focal point is availability and uptime … not security,”” says Kevin Beaver, principal information security consultant at Principal Logic. The problem extends to SOC 2 audits, he continues. These reports “”often paint a rosy picture in terms of security … but actual vulnerability and penetration testing that highlights technical flaws is also needed.””
A sense of complacency can be fatal, Gartner’s Riley adds. “”Over the last decade we’ve gone from, ‘I’ll never trust cloud computing to be secure’ to ‘It has to be more secure because AWS, Microsoft, and Google are offering these services.'”” However, cloud security failures are more common than ever, he points out. What’s more, “”They’re almost always the fault of the customer for not appreciating that they have the primary responsibility and taking time to ensure that everything is configured properly.””
Too often, designers and end users overlook basic settings, such as open file shares, Riley adds. “”Although they are supposed to be locked down by default, they are not. A lack of controls allows someone to go in—perhaps a developer—to simplify things. Unfortunately, in the process, they inadvertently share everything with the world.””
The upshot? “”The cloud is a more secure starting point than your own data center, because instead of the whole stack, you only have to secure certain slices of the stack,”” Riley explains. “”But the attention you have to pay to those slices is much greater than before. You have to start from a zero-trust framework and focus on the principle of least privilege.””
A Clearer View
A starting point for improving cloud security is to build a more expansive and nuanced framework that hinges on three key areas: managing security across a diverse array of devices and SaaS services in different locations, including at the edge; establishing security beyond a single data center or location and replicating the security everywhere; and maintaining a complete view of settings and protections across cloud providers and clouds.
A security plan must be flexible enough to scale as an organization adds systems and software, while recognizing that some data is more valuable than other data. This points to the need for a more comprehensive security-by-design framework, centralized visibility and controls, continuous compliance monitoring and reporting, the ability to monitor and track the threat landscape, and a plan for dealing with a breach or other security incident when it occurs.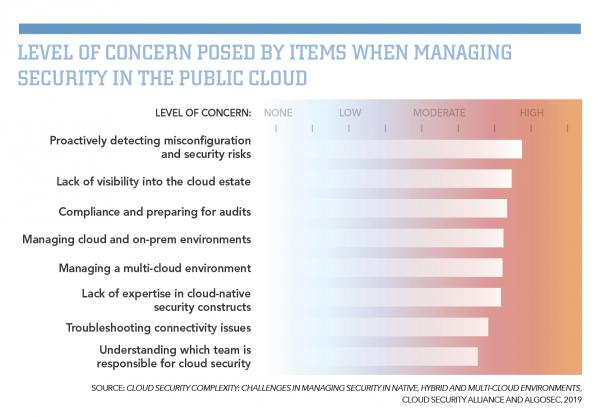
More security, Optiv’s Vadakkan says, isn’t necessarily better security. “”You have to think about security less as a stopgap measure and more as a framework that has to be woven into private, public, and hybrid clouds. There’s a need for smarter systems and greater automation.””
Understanding the value of data and conducting a thorough cost-benefit analysis shines a light on the process. “”The key is to bring all the various components and pieces under the umbrella of an information security program,”” Beaver explains. All of this, in turn, helps cloud security designers better understand the nuances of web applications, data flow, network designs, cloud infrastructure, and improved data governance. “”Beyond that, just as with traditional networks, it’s all about visibility and control,”” he adds.
Eye on Tools
While cloud providers offer a growing array of security tools—often at no additional charge—control frameworks such as the Cloud Controls Matrix offered by CSA and activity monitors that fall into the cloud access security broker (CASB) category are essential. These solutions, among other things, introduce trust ratings, trust levels, digital watermarks, behavioral analysis, permissions and automated API detection, and encryption support. Many CASBs also monitor SaaS applications as well as other applications running in Java Virtual Machines.
Data encryption at rest and in motion are critical too, Riley says. This includes hardware-based encryption that a cloud provider offers. “”There’s a misconception that encryption slows performance. This simply isn’t the case,”” Riley says. And while some businesses may balk at spending more time and money to encrypt everything, the dollars saved can easily backfire. “”If you selectively encrypt data, you’re basically saying that you can get 100% of your classifications right, and if something goes wrong, you can stand in front of an auditor or regulator and explain the problem away.””
Multifactor authentication (MFA) can also be used to protect accounts, containers, folders, and more. Vadakkan notes that only about 7% of companies with clouds use the technology consistently, and that the resulting lack of protection frequently leads to gaping holes in security. What’s more, if an attacker steals someone’s credentials, no amount of protection—including encryption—will impede this individual. By incorporating the principle of least privilege into applications and systems, controlling permissions carefully, and using physical and virtual tokens to authenticate through MFA, Riley says, an enterprise can dramatically reduce unauthorized access to data along with its overall risk profile.
Yet, even with the most robust cloud security in place, you must plan for the worst. If a distributed denial-of-service attack occurs or ransomware seizes systems and data, your customers can sidestep much of the pain if there is a backup and data recovery solution in place. Having failover capabilities mapped out before a breach or breakdown occurs is critical too. This, among other things, requires your customers to reassess current availability resources as well as the service infrastructure used for e-commerce, internal business operations, and other important tasks—areas in which you can guide them.
Beyond the Clouds
Cloud security is continuing to evolve, Vadakkan says, so it’s wise to keep an eye on emerging auto-remediation tools, which automate cybersecurity tasks such as scanning for vulnerabilities and fixing flawed configuration settings. In most cases, these applications can be integrated with other security applications and tools offered by the cloud service or a third-party security provider.
Cloud security posture management (CSPM) is another tool that’s gaining traction. Riley advises organizations to resist “”duplicating their on-premises stacks and instead look for ways to be as cloud-native as possible.”” However, he adds, “”It’s impossible using only native controls to have consistent security policies across multiple clouds.”” CSPM offers key advantages: It abstracts the security pane from cloud deployments, which makes it easier to manage policies and systems; and it frees developers from waiting for others to provision servers and test security settings. “”CSPMs provide valuable guardrails for operating within security policies,”” he says.
In the end, it’s crucial for channel pros to recognize that every advance in technology introduces new and sometimes more sophisticated ways for attackers to infiltrate systems and damage or steal data. As the volume of data swells, APIs proliferate, and connection points grow in numbers and complexity, MSPs must remain vigilant and adopt cloud security protections that foster agility and flexibility while reducing risk for their customers.
“”The cloud represents a huge disruptive shift in terms of both architecture and security,”” Yeoh says. “”It redraws boundaries. There’s a perception that the cloud complicates security, but if security is done right, it can actually improve protection and simplify things.””















