New Cybersecurity Threat Report Released
As if MSPs didn’t already have enough to worry about, the newly released 2025 OpenText Cybersecurity Threat Report reads like a flashing red warning light for anyone responsible for securing client networks. From AI-powered phishing and resurgent ransomware to malware infections surging in places you’d least expect, the message is clear: The threat landscape is both evolving and escalating.
Here’s a breakdown of what matters most for channel pros, backed by data and insights from OpenText’s global telemetry and expert analysis.
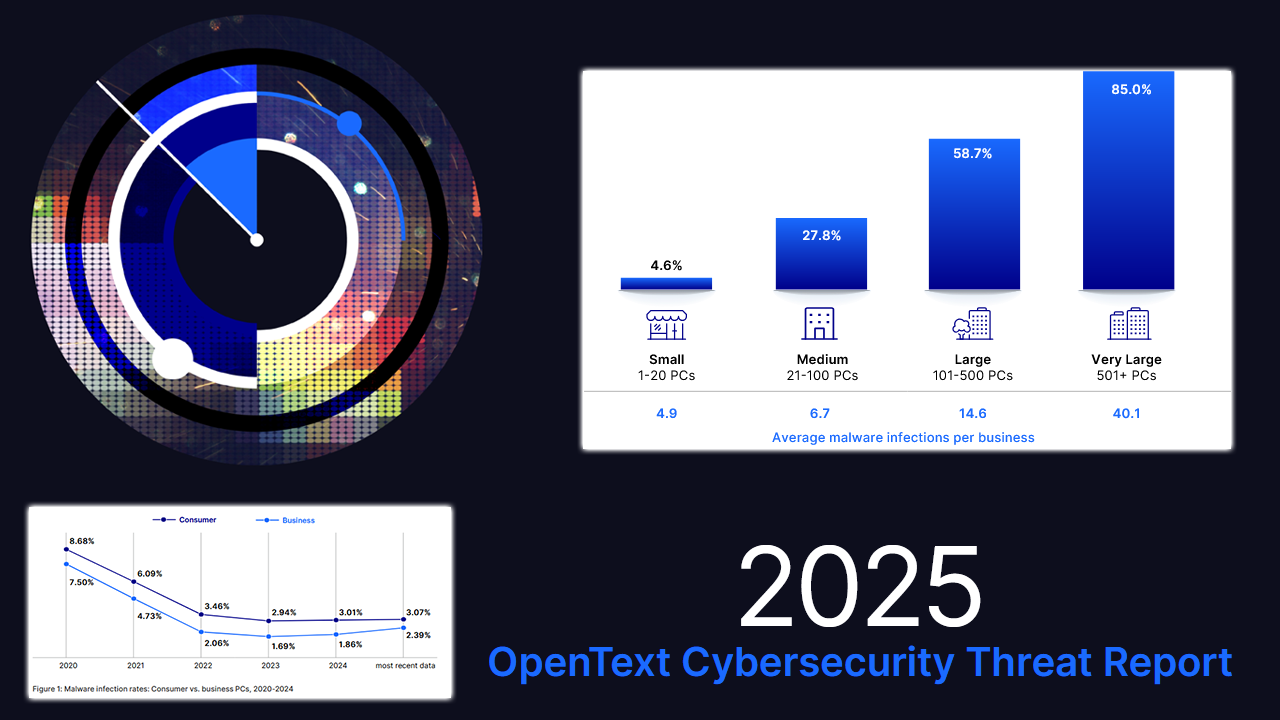
Malware: Business Infection Rates Surge Over 28%
If you were hoping 2023’s slight uptick in malware infections was a fluke, prepare for disappointment. The cybersecurity threat report shows a 28.5% year-over-year increase in business PC infection rates — jumping from 1.86% in 2023 to 2.39% in 2024. That’s the highest since 2020 and a troubling reversal of a multiyear decline.
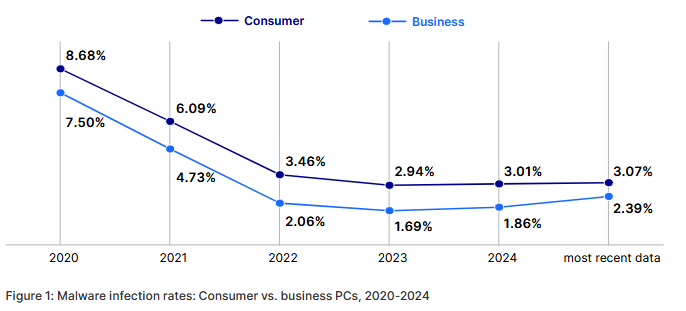
Business infections now account for nearly three quarters of all newly detected malware files (73.8%). Most threats still rely on tried-and-true tactics, like hiding in common file system locations.
“The idea that attackers are eroding the effectiveness of established cybersecurity teams should give business leaders pause,” the report warns.
Size Doesn’t Equal Safety
Small businesses may think they fly under the radar, but the impact of even a few infections can be devastating. OpenText’s cybersecurity threat report showed that 4.6% of businesses with fewer than 20 endpoints experienced malware infections, with an average of 4.9 infected PCs. That number jumped to 85% for companies with 500-plus endpoints, impacting over 40 devices on average.
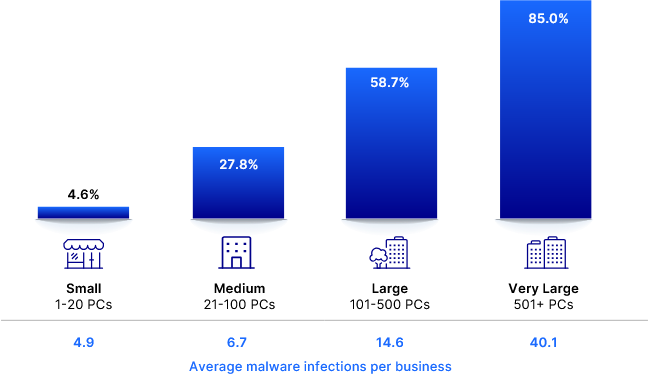
In other words, even a “small” breach can be a big problem, especially for MSP clients without enterprise-grade resources.
Enter ‘Extortionware’
Ransomware hasn’t gone away. It has just evolved.
While traditional encryption attacks persist, a new favorite among threat actors is “extortionware.” This basically is data exfiltration without encryption. It seems that cybercriminals would rather skip locking up files and instead steal sensitive data, threatening to leak it unless paid. It’s faster, sneakier, and arguably more damaging.
About 48% of survey respondents said their company had been hit with ransomware, and nearly half of those victims (46%) paid the ransom. Interestingly, 97% said they were able to recover their data using backups or a decryption key from the attacker.
Still, a large number of businesses ended up paying, even when data recovery was possible via other methods. Why? Reputational damage. “Resilience can’t stop at recovery,” says Senior Security Analyst Tyler Moffitt. “If your data has value, you’re a target and reputational damage is the new ransom.”
Supply Chain Shocks and Air-gapped Realities
A staggering 62% of ransomware victims said the attack originated from a software supply chain partner, leading 91% of all survey respondents expressing concern about third-party breaches.
It’s not just talk, either, according to the report. Nearly half said they’re considering switching vendors over security concerns. For MSPs, this is both a risk and a revenue opportunity. There’s never been a better time to pitch supply chain audits, vendor assessments, and compliance-as-a-service offerings.
AI Is Now the Enemy (and the Tool)
The report drives home what most security pros already know: Generative AI is supercharging phishing campaigns. Attacks are more personalized, more convincing, and harder to spot.
Nearly 45% of companies reported a noticeable uptick in phishing tied directly to AI proliferation. Spearphishing now accounts for the majority of attacks in peak months, and ZIP files — often password protected — are the new go-to for malware delivery.

“Phishing attacks are shifting away from traditional ‘spray and pray’ tactics,” said Troy Gill, senior manager of threat research. “Cybercriminals are moving toward more sophisticated, highly targeted attacks.”
Even trusted cloud services are being weaponized. In 2024, attackers abused legitimate platforms like Google APIs, AWS, and Canva for phishing campaigns. Why? Because your firewall won’t block them.
What MSPs Should Do (and Tell Their Clients)
The report closed with the hard truth that no solution is perfect. It’s not a matter of “if” but “when.” OpenText’s recommendations largely aligned with services most MSPs already offer, but the company also presents a compelling checklist to validate or enhance your portfolio.
Here’s the “must-do” list, according to OpenText:
- Endpoint and DNS protection, which together reduce malware infections by up to 19.4%
- Regular phishing and security awareness training
- Frequent, immutable, and air-gapped backups
- MFA everywhere … yes, everywhere
- Regular incident response testing and table-top exercises
- Real vulnerability management and not just patching Windows every month
- Vendor and supply chain security assessments
“The urgency of the situation is clear …
When your business is at stake, comprehensive security is non-negotiable.”
With geopolitical uncertainty, blurred lines between state and criminal threats, and AI in the hands of attackers, the case for managed security has never been stronger.
The reality is, many SMBs won’t be able to keep up. As the threat surface expands and cybercrime professionalizes, the role of MSPs will shift from IT provider to risk management partner.
That’s not just a challenge. It is, in fact, a massive opportunity.
Images: OpenText