My consulting company recently received network scans done for a HIPAA security risk analysis of a healthcare client that is working with an MSP. That MSP has these promises on its website:
- We provide best-practice cybersecurity and HIPAA compliance to healthcare organizations that you can rely on.
- We monitor your systems 7/24 to make sure there are no security weaknesses. Weaknesses are immediately identified and patched for maximum security at all times.
- We will regularly assess your network and implement any changes needed to help you stay compliant and avoid the consequences of a compliance violation or data breach.
Sounds great, doesn’t it?
But is it true, or just hype?
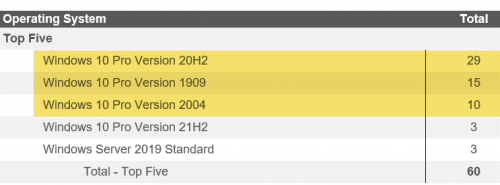
Considering that the healthcare client’s November 2022 computer inventory shows that 54 of their 60 computers (90%) are using operating systems no longer supported by Microsoft with security patches and updates, I’m leaning toward hype.
Microsoft’s Windows 10 Lifecycle website shows that the 29 Windows Pro Version 20H2 systems lost their security patches in May 2022. The 10 Windows 10 Pro Version 2004 systems lost their security patches in December 2021, and the 15 Windows Pro Version 1909 systems (25% of the total number) haven’t received patches and updates since May 2021—a full 18 months before our assessment scans.
The Cybersecurity and Infrastructure Security Agency (CISA) has identified unsupported operating systems and software as the No. 1 Bad Practice to avoid. HIPAA and other regulations require covered entities to only use operating systems and software supported by security patches and updates. Consider this from a 2018 federal HIPAA newsletter dedicated to patching systems: “identifying and mitigating the risks unpatched software poses to Electronic Protected Health Information (ePHI) is important to ensure the protection of ePHI and in fulfilling HIPAA requirements…”
Making matters worse, based on information provided by their MSP, our healthcare client attested on the application for their $2 million cyber insurance policy that their systems are patched, even though 90% of their 60 systems have unsupported operating systems. Cyber insurance requires that a client implement the cybersecurity to which they attested on their insurance application, otherwise their claims can be denied. For example, in July 2022, Travelers Insurance sued a client for misrepresenting its cybersecurity on its insurance application. Within two months, Travelers’ client agreed that the policy should be cancelled, and the ransomware claim denied.
The bad news for the MSP is that their unmet promises to this healthcare client aren’t just in the fine print of a contract—they are on the company website.
It’s a bad day when an MSP’s own advertising proves that they are either a liar or just careless.
In this case, either choice leaves their client open to cyberattacks, regulatory compliance penalties, lawsuits, and a claims denial of their $2 million cyber liability insurance policy if they are hacked.
While the unsupported computers are certainly a huge risk to the HIPAA-regulated client, what about the risk to the MSP if they have the same exclusion we have in our Errors & Omissions (E&O) insurance policy?
The coverage under this Policy will not apply to any Loss arising out of:
Deceptive Business Practices, Antitrust & Consumer Protection – any actual or alleged false, deceptive or unfair trade practices, antitrust violation, restraint of trade, unfair competition, violation of consumer protection law, false, deceptive or misleading advertising, inaccurate cost estimates or failure of goods or services to conform with any represented quality or performance.
If the client sues the MSP, the MSP’s E&O insurance will likely deny their claim because of the false advertising exclusion. That could make the MSP pay out-of-pocket for $2 million in incident costs plus additional damages and legal fees.
So, is this MSP lying or just careless?
I’m thinking a little of both, but not in the way you might guess.
I don’t think they are lying to their prospects and clients, but I do think they are lying to themselves.
They are so proud of themselves that they believe the hype on their website. They may belong to a peer group. They may have a great marketing engine. Their owner may have won a Chamber of Commerce award and been recognized by their peer group organization or elsewhere in the IT industry. The company is one of the Best Places to Work in _______ . The MSP owner trusts his team.
But the fact is that the owner isn’t validating that his team is delivering on their promises. He trusts his team to the point that he isn’t checking what they are really doing—and not doing. His company isn’t offering “best-in-industry IT support” when 90% of the systems at a regulated client have unsupported operating systems. (Ninety percent isn’t a margin-of-error number; it’s evidence of nonexistent quality control.)
He has all the reporting tools to find the same evidence we did, but he hasn’t used them.
He hasn’t looked to see that his processes aren’t meeting the basic standards of his industry, leaving him open to paying the costs when his E&O insurance won’t cover him.
He probably would be shocked to learn that his successful company could go under with millions of dollars in lawsuit settlements not covered by insurance. This MSP owner hasn’t realized that if that happens, his staff will all quickly get new jobs, and he will be left with years of debt. He would certainly not be the first. For example, a business was put on a 20-year fraud penalty program by the Federal Trade Commission (FTC) for false advertising by displaying a HIPAA Seal of Compliance on its website and then failing a HIPAA investigation. In addition, my article “MSP Sued!” talked about an MSP being sued for not delivering on the promises it advertised and, included 10 things you can do to protect yourself.
What should this MSP owner do differently? He should use his reporting tools and spend part of each week analyzing client networks to validate he is living up to his promises.
Regulatory penalties and lawsuits are public. He should realize that it is his name and reputation that will be smeared by not validating the work of his team.
If you make promises in marketing—but don’t validate that your team is delivering—you are lying to yourself and risking legal jeopardy.
Warren Buffet once said, “It takes 20 years to build a reputation and five minutes to ruin it. If you think about that, you’ll do things differently.”
So, what are you going to do differently?
MIKE SEMEL is a former MSP and founder of Semel Consulting, which provides advisory services to MSPs and end users for compliance, cybersecurity, and business continuity planning. He worked with CompTIA to develop its Security Trustmark Plus, and with RapidFire Tools to create Compliance Manager GRC.