MSP Technology News Headlines
Cisco leads the headlines for this week, but there’s also a lot of interesting technology news from all over the industry. From cybersecurity to career growth to partner program enhancements, you’ll want to stay in the know. Ready for a quick rundown of this week’s MSP news and partner program updates? Scroll on down!
CISCO REPORT: Privacy Landscape Grows Increasingly Complex in the Age of AI
Cisco’s 2025 Data Privacy Benchmark Study reveals increasing trust in global providers to protect and secure data.
Key stats from the press release:
- 86% of respondents support privacy legislation, recognizing its positive impact on business operations.
- While 96% confirm that privacy investments provide returns exceeding costs, organizations anticipate resources and spending will likely shift to AI in the coming year.
- AI familiarity is rising, with 63% being very familiar with generative AI, but concern for unintended risks continue.
Alvaka’s Ransom Recovery Resources Now Available to Ingram Micro’s US Channel Partners
As ransomware attacks surge in 2025, Alvaka and Ingram Micro help educate and enable channel partners with better cyber practices and remediation solutions.
Key quote from the press release:
“As a long-trusted industry peer and one of the top three ransomware recovery firms, Alvaka helps organizations quickly and successfully recover from ransomware attacks and retain their clients during and after these highly volatile cyber events. With Ingram Micro’s extensive reach, community leadership, and cybersecurity market expertise, we will be able to help more businesses with the support they desperately need to recover from and ready for these devastating attacks.” — Oli Thordarson, founder and CEO, Alvaka
N‑able Expands Its Ecoverse With Key Technology Alliance Program Integrations, Enhancing Cyber Resilience and Operational Efficiency
Integrations with top-tier third-party vendors expand the company’s platform with cutting-edge solutions to meet evolving IT and cybersecurity needs.
New integrations from the press release:
- Xurrent: An AI-powered ITSM platform designed to help IT professionals significantly enhance automation and service management capabilities. Xurrent ITSM enables automated ticket creation, intelligent workflow automation, and real-time system monitoring directly within N-central.
- SeedPod Cyber: Cutting-edge AI-driven Insurtech platform, now integrated with N-central, that provides a seamless experience to partners seeking to offer their clients streamlined cyber insurance solutions, in addition to Tech Errors & Omissions (Tech E&O) insurance for themselves.
- ScalePad Lifecycle Manager: An advanced platform for automating the lifecycle management of IT assets, now supports an enhanced integration for further enrichment of asset data in N-central, enhancing resilience, efficiency, and service delivery for our shared partners.
- Rewst: Building on the success of Rewst’s integration with N-central, this collaboration now includes an integration with Cove to streamline day-to-day operations by allowing users to automate processes such as user and device onboarding, backup monitoring and ticketing, and billing and invoice reconciliation.
- Derdack Signl4: A powerful mobile incident management and notification platform that integrates with N-central, Signl4 delivers fast, automated notifications for critical incidents, helping businesses respond to urgent threats and operational issues in real-time, reducing downtime and minimizing risk.
- Webroot by OpenText DNS Protection: DNS protection that integrates with N-central and N-sight to deliver enhanced cybersecurity features, offering the ability to block malicious websites and prevent phishing attacks, ensuring a higher level of security for end-users while reducing operational risks.
SOPHOS REPORT: In 56% of Sophos IR and MDR Cases, Adversaries Logged In, Instead of Breaking In
IR and MDR cases highlight attackers are exfiltrating data in just three days. Compromised credentials top root causes for second year.
Key stats from the press release:
- The primary way attackers gained initial access to networks (56% of all cases across MDR and IR) was by exploiting external remote services. This included edge devices such as firewalls and VPNs, by leveraging valid accounts.
- The combination of external remote services and valid accounts aligned with the top root causes of attacks. For the second year in row, compromised credentials were the No. 1 root cause of attacks (41% of cases). This was followed by exploited vulnerabilities (21.79%) and brute force attacks (21.07%).
- Akira was the most frequently encountered ransomware group in 2024, followed by Fog and LockBit. This was despite a multigovernment takedown of LockBit earlier in the year.
Read more insights on the 2025 Sophos Active Adversary Report in the Sophos blog.
Todyl Partners with SPECTRA to Revolutionize Cyber Insurance Solutions for MSPs and Their Clients
The partnership helps MSPs tackle cyber insurance challenges for SMBs with better coverage, easier procurement, and warranty-backed security services.
Key benefits from the press release:
- Service Warranty Protection: MSPs can differentiate their security offerings by including robust warranty-backed services with clear, tangible financial guarantees, delivering greater confidence, trust, and competitive advantage in the marketplace.
- Eliminates Complex Questionnaires: Certified MSPs help clients bypass the lengthy technical questionnaires typically required for cyber insurance.
- Preferred Coverage Programs: Clients gain access to policies backed by institutional carriers including Lloyd’s of London syndicates, with straightforward terms and fewer exclusions, reflecting their investments in security.
- Reduces Premiums: Clients have secured premium reductions of up to 36%, even in high-risk industries, or customers with incident history, including those who were previously denied coverage.
- Efficient Procurement: Get insurance quotes delivered through broker partners in as little as 24 hours compared to sometimes weeks or months through traditional channels.
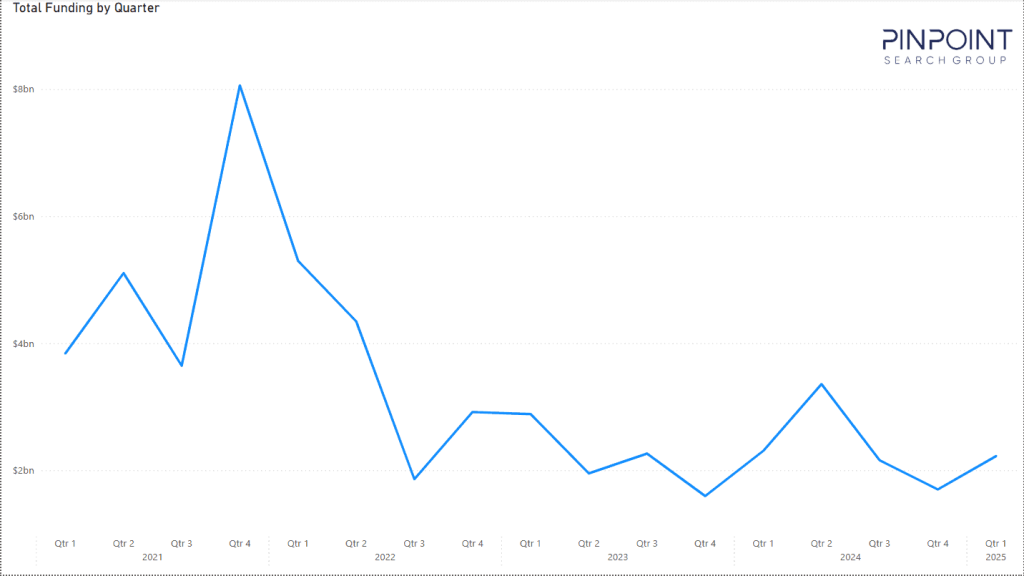
PINPOINT SEARCH GROUP REPORT: Cybersecurity Vendor Funding in Q1 2025
Key stats from the press release:
- Deals rose an overall 12% when compared with Q1 2024. This signaled stabilization and interest in investment in cybersecurity businesses, despite a slight decline of 4% in funding raised when compared to the same period during the previous year.
- Pinpoint Search Group’s research team recorded a total of 103 cybersecurity vendor transactions, including 85 funding rounds, 17 M&As and one IPO.
- A total of $2.2 billion was raised, a slight decline compared with the $2.3 billion raised in Q1 2024. Still, this indicates signs of market stability in the cybersecurity space.
- The data details how 85 funding rounds were tracked in Q1 2025, representing a 12% increase in funding volume compared with the first quarter of 2024, which saw 77 funding rounds. This is something positive for investors to consider.
Pia Reveals Strategic Reorganization, Leadership Appointments to Drive Growth Acceleration
Strategic organizational changes are set to position the company for its next growth phase.
Key highlights from the press release:
- Pia has aligned all of its go-to-market functions under one unified vision. The goal is to have everyone working closely toward common growth objectives and partner-focused outcomes.
- Nic Ferraro, formerly chief strategy officer, now is chief revenue officer (CRO) — a company first.
- Pia established a dedicated technical sales team focused on pre- and technical sales functions. This will increase capacity for product demonstrations, thereby improving sales conversion rates and reducing sales cycle times.
SonicWall Enhances Secure Connectivity for Leading MSP With Cloud Secure Edge (CSE) for Zero Trust Access and Authentication
Showtech Solutions chooses SonicWall’s cloud-native ZTNA solution for its seamless user experience, advanced security features, and flexible traffic routing capabilities.
Key quote from the press release:
“CSE has significantly reduced user VPN calls related to password resets and multifactor authentication issues by allowing us to use different identity providers for authentication. The ability to install remotely with zero end-user interaction was also a key requirement. Personally, I rely on it for administering various client systems, especially since much of our access is tied to our WAN IP. It’s incredibly helpful to access resources local to our office, even when I’m working remotely.” — Chase Kyler, systems engineer, ShowTech Solutions
Bugcrowd Launches New MSP Offering to Address Pentesting Backlog
New offering introduces a scalable solution for fast-tracked, crowd-powered compliance requirements.
Key capabilities from the press release:
- Comprehensive Services: MSP Pentesting capabilities include networking, API’s, web, mobile apps, and cloud configuration testing.
- Standardized Delivery: Managed by Bugcrowd, program methodology consistently provides a reliable and standardized approach to pentesting.
- Short Stand-up Time: Partners can launch engagements in as little as three business days, ensuring rapid response times for urgent compliance needs.
- RapidRevenue: Partners can benefit from faster revenue recognition through faster initiation of engagements, making it financially advantageous for MSPs.
BARRACUDA THREAT SPOTLIGHT: The Good, the Bad, and the ‘Gray Bots’ – the GenAI Scraper Bots Targeting Your Web Apps

Key quote from the blog post:
“GenAI gray bots are blurring the boundaries of legitimate online activity. They can scrape vast volumes of sensitive, proprietary, or commercial data and can overwhelm web application traffic and disrupt operations. Frequent scraping by these bots can degrade web performance, and their presence can distort website analytics, leading to misleading insights and impaired decision-making. For many organizations, managing gray bot traffic has become an important component of their application security strategies.” — Rahul Gupta, senior principal software engineer, Application Security Engineering, Barracuda
vRx by Vicarius Is Now Available for Purchase on the CrowdStrike Marketplace
vRx leverages real-time and high-fidelity security data from the CrowdStrike Falcon cybersecurity platform to provide instant and automated remediation, supporting over 10,000 products and across Windows, Linux and Mac operating systems.
Key benefits from the press release:
- By leveraging innovative vulnerability detection capabilities and actionable insights from CrowdStrike Falcon Exposure Management, Vicarius vRx empowers customers to remediate vulnerabilities at scale, going beyond traditional patching methods.
- Through Vicarius, customers can address vulnerabilities with a diverse range of solutions such as advanced cross-platform patch management, workarounds, worklets, and in-memory virtual patching.
- The integration of CrowdStrike with Vicarius vRx further streamlines the remediation process with real-time and automated patching and seamless correlation across 3rd party solutions, allowing joint customers to directly address identified vulnerabilities within the vRx platform.
SolarWinds Unveils Next-gen Solutions to Tackle Modern IT Operational Resiliency Challenges
New capabilities integrate observability, incident response, service management, and AI automation capabilities designed to streamline IT and strengthen operational resilience.
Key features of the expansion from the press release:
- SQUADCAST Incident Response: New addition unites people, processes, and technology, providing a proactive, structured approach to incident response and resolution.
- SolarWinds Observability: Supports expanded hybrid IT awareness with deeper and broader single-pane-of-glass visibility across all major cloud vendors. This includes GCP, AWS, Azure, and on-premises environments.
- SolarWinds Database Observability: Automatically analyzes query patterns and suggests optimal query rewrites to improve database queries. This delivers more accurate and efficient query optimization.
- SolarWinds Service Desk: Automates compiling and formatting pre-written operational guides into new Runbooks with standardized resolution processes. This enhances operational efficiency and improve incident response times.
Freshworks Launches New Partner Program with Expanded Reseller and Services Offerings
Uncomplicated service software, flexible engagement models, and a new services delivery program help Freshworks partners accelerate time to value.
Key benefits from the press release:
- Flexible Sales Engagement Models: Partners can choose the business model that best fits their needs. Options range from one-time commissions as sales consultants to ongoing revenue opportunities as authorized resellers, premier resellers, or service providers.
- New Offering for Service Delivery Partners: System integrators and solution providers offering professional services can now join a new program that provides training, certifications, and direct engagement with Freshworks’ sales teams, with leads shared directly with them.
- Faster Impact for Partners and Customers: Freshworks’ people-first approach empowers partners to manage the full customer lifecycle with specialized enablement, certifications, and direct access to Freshworks experts and resources. Premier resellers benefit from recurring margins on every sale, full control over billing and renewals, and deeper customer relationships.
- Enhanced Partner Services and Support: Partners will receive increased regional sales support, marketing development funds, enablement and internal alignment. The Freshworks Professional Services team will also provide key technical enablement and onboarding training in addition to opportunities for partner services delivery across markets and business segments with a refreshed sponsorship model to ensure partner success.
Contrast Security Announces Channel-first Strategy to Accelerate Next Stage of Growth
Significantly expanded partner program increases joint go-to-market investments and enables a wider network of solutions providers to deliver unmatched application security solutions.
Key quote from the press release:
“Organizations are frustrated with legacy AppSec approaches that create bottlenecks and fail to stop real threats. By going channel-first, we’re amplifying our ability to deliver real-time attack prevention and vulnerability monitoring to more enterprises — through the trusted advisors they already rely on.” — Scott O’Rourke, chief revenue officer, Contrast Security
Keepit Presents Roadmap for the Future of Data Protection
Keepit’s product roadmap is designed to future-proof the cyber resilience of organizations navigating an increasingly complex threat landscape.
Key enhancements from the press release:
- Covering More Cloud Apps: From eight to hundreds in three years
- New Domain-specific Language (DSL) introduces the ability to back up and recover data from many more SaaS applications. The rollout begins with seven applications in 2025 — Jira, Bamboo, Okta, Confluence, DocuSign, Miro, Slack — with rapid expansion to follow. The ultimate goal is full coverage of all SaaS applications used by enterprises, spanning HR, finance, sales, production, and more.
- New and Improved Capabilities: One source of data truth
- Anomaly Detection: Provides enhanced monitoring, compliance, and security insights, enabling proactive identification of irregularities. Anomaly detection will be available to Keepit customers in early May 2025.
- Data Protection Dashboards: Offers centralized control and simplified reporting, enhancing visibility and management of data protection efforts. Data protection dashboards were made available to Keepit customers in January 2025.
CompTIA Updates A+ Certification to Meet the New Demands of Tech Support
New exams have increased emphasis on cybersecurity, cloud computing and other areas.
Key areas of emphasis from the press release:
- Basic AI concepts, including appropriate use, limitations to consider, and understanding the differences between private versus public data
- Cybersecurity measures, protocols, and tools for malware detection and prevention. This reflects the growing need to safeguard systems and data against increasingly sophisticated cyber threats.
- Cloud computing models and virtualization concepts to support today’s IT infrastructures
- Software troubleshooting to diagnose and resolve software issues in complex environments while maintaining system functionality and minimizing downtime
- Understanding robust networking solutions — including VPNs and secure remote access — along with the ability to connect, configure and troubleshoot a wide array of network devices
eMazzanti Technologies Named to Inc. 2025 Regional Fastest-growing List
Woman-owned cybersecurity firm is honored for its growth for the 11th straight year.
Key quote from the press release:
“eMazzanti’s trained, responsive and professional staff works diligently to advise large and small businesses on cybersecurity, artificial intelligence, outsourced network management, and other mission-critical issues and services. More companies than ever before are adopting digital solutions, and we pleased to help them customize, improve, and secure their networking and other environments against threats from nation/state and other bad actors.” — Jennifer Mazzanti, co-founder and CEO, eMazzanti Technologies
EnGenius Transforms Security Monitoring with Context-aware AI Intelligence

New cloud-based surveillance platform combines edge and cloud AI capabilities. Without relying on traditional NVRs, it leverages AI to provide advanced contextual recognition and intelligent security features.
Key quote from the press release:
“What truly sets our system apart is its ability to analyze contextual sequences rather than just single-frame images, enabling preventive alerts before incidents occur. For example, our Cloud AI can identify fatigued and inattentive workers on a manufacturing line and send alerts to managers, preventing accidents before they happen.” — Roger Liu, executive vice president, EnGenius Technologies
Exabeam Nova Unleashes the Future of Agentic AI in Cybersecurity
Proactive multi-agent experience uplevels the SOC, enables security leaders, analysts, and investigators to increase productivity and impact.
Key benefits from the press release:
- Autonomous AI agent Exambeam Nova delivers actionable intelligence that enables security teams to respond faster to incidents, reduce investigation times by over 50%, and mitigate threats more effectively.
- Exabeam is now the first and only security operations vendor delivering a multi-agent experience where specialized AI components are integrated throughout the security operations workflow.
- Unlike passive AI assistants that merely retrieve and synthesize data, Exabeam Nova automatically correlates multiple attack signals, actively investigates cases, and classifies threats based on real-world behavioral context for an up to 80% increase in analyst productivity.
Combatting Cyber Threats with AI: Darktrace and Climb Channel Solutions Sign Distribution Agreement for North America
Under the agreement, Climb Channel Solutions will now distribute Darktrace’s portfolio of AI-powered cybersecurity products across North America.
Key quote from the press release:
“Partners play an essential role in helping to protect customers against the rapidly evolving threat landscape. Our collaboration with Climb expands the reach of Darktrace’s solutions across North America to help more organizations increase their cyber resilience and take a more proactive approach to cybersecurity. Together, Darktrace and Climb are equipping partners with the tools they need to deliver best in class AI-powered cybersecurity solutions to customers.” — Dan Monahan, chief partner and transformation officer, Darktrace
RSAC Expands Beyond Flagship Conference
RSA Conference LLC rolls out a community-driven membership platform that enables the world’s cyber defenders to address the ever-evolving and escalating cybersecurity threat environment.
Key features from the press release:
- RSAC™ Community Platform provides several features, including:
- Cybersecurity AI Co-Pilot: AI interface that allows members to learn, solve problems, and uncover insights by drawing on the vast number of authoritative RSAC presentations, ideas, discussions, tutorials, and other curated content
- Library: A centralized hub with video presentations, podcasts, webcasts, and expert sessions in a comprehensive, easy-to-navigate repository
- Daily News Brief: Curated daily summarization of recent/current cybersecurity news, provided to members through the platform
- Groups: Provides RSAC Community Members and leaders with a dedicated space to discuss cybersecurity topics and collaborate
- Secure Chat: Gives RSAC Community Members a space to grow and build their network. Allows for secure and private conversations with contacts.
- Membership features both free and professional tiers, and is accessible through a browser and a dedicated mobile app.
Kaseya Expands Data Center Capabilities in South Africa
As a response to increasing demand from South African customers and partners in the region, data center storage now offered to support Microsoft 365 backups.
Key highlights from the press release:
- Through this data center, Kaseya also supports endpoint backup, with business continuity and disaster recovery to soon be offered.
- South African businesses must adhere to the Protection of Personal Information Act (POPIA). Further regulation introduced in 2024 — the National Policy on Data and Cloud — also enforces stricter data security and data sovereignty controls.
- With data centers in-region, customers can rely on faster backups, which improves their recovery time objective (RTO). It also makes it easier to ship hard drives in and out of the data center in cases where large amounts of data need to be transported.
Hornetsecurity Group to Acquire Altospam, a Leading French Email Security Provider
This latest acquisition would complement Hornetsecurity’s strategy to provide European-built cybersecurity solutions to businesses and organizations worldwide.
Key quote from the press release:
“As a respected European developer, Altospam’s core goals closely align to Hornestsecurity’s overriding mission to create a safer world through our next-gen, cloud-based cybersecurity services, resulting in overall synergies to the benefit of partners and customers alike.” — Daniel Hofmann, CEO, Hornetsecurity
Images: iStock, Pinpoint Search Group, Barracuda, EnGenius Technologies via PR Newswire