On September 2, the Cybersecurity and Infrastructure Security Agency (CISA), part of the U.S. Department of Homeland Security (DHS), publicly warned businesses about outsourcing IT support to managed service providers. Use that warning as a great opportunity to market yourself.
CISA said working with an MSP “”can introduce unanticipated risks to an organization”” and that “”vulnerability may increase as potential vulnerabilities in the (MSPs’) networks are compounded with any unresolved vulnerabilities on the organization’s systems.””
In other words, your clients have double to worry about—their systems AND YOURS. You can choose to feel threatened and become defensive, or be smart and use the CISA warning as a marketing tool to be seen as a cybersecurity and compliance authority, build confidence in your services, and differentiate your company.
After the recent high-profile attacks on the client network management tools used by MSPs that spotlighted the industry, it makes sense that businesses understand the risks they face when outsourcing IT services.
CISA is just saying out loud what many are thinking. I’m not surprised at the warning, since I wrote “”How to Protect Your Clients from…You”” (2019) and “”MSP SUED! Are You Ready?”” (2020), which both discussed the risks MSPs create for their customers. Your employees have top-level privileged access to your clients’ networks that contain sensitive and regulated information. You back up that data into systems that you or your vendors manage. If you get hacked your customers get hacked. If you cause their data to be breached, or they get shut down by ransomware, they suffer the consequences.
Why should they trust you?
Show them.
CISA’s Recommendations to Your Customers
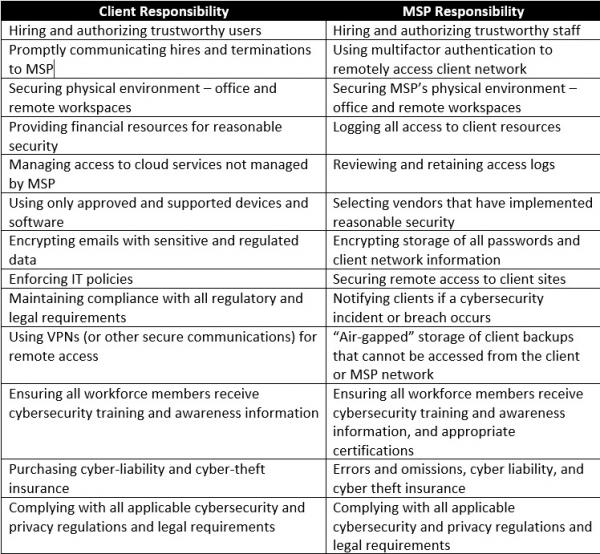
CISA makes it clear that business owners can’t simply outsource their risks to an MSP; it is a shared responsibility. Here are the 11 things CISA says customers should demand of MSPs in a contract and a documented Shared Responsibility Model:
- Specific performance-related service-level agreements, including a clear delineation of operational IT services and security services.
- Confirmation that the individual signing for the MSP is responsible for the product’s security or service and a requirement to notify the customer of any change of MSP ownership or leadership and internal MSP measures to ensure the security of the organization’s data.
- Detailed guidelines for incident management, including the MSP’s incident response responsibilities, warranty information, compensation for service outages, and plan to provide continuous support during a service outage.
- Remediation acceptance criteria that define the steps the MSP will take to mitigate known risks.
- A Software Bill of Materials (SBOM) or similar verification of the security of any software the MSP will use to provide its services.
- Statement from the MSP on how data from different clients will be segmented or separated on the MSP’s networks.
- Detailed guidelines for log and records maintenance, including requirements for the MSP to provide secure storage of backups and for detailed records of when accounts are accessed, by whom, for how long, and what actions were completed.
- This should include physical access to storage, networking, and processing capabilities.
- Documentation of employee vetting (including subcontractors and independent consultants) to minimize risks of intellectual property theft, manipulations, or operational disruptions.
- Direct access to security logging information, network intrusion detection, and anomaly analysis data telemetry from all systems managed by the MSP that support the service being procured.
- The ability for the customer organization to examine the systems that directly and indirectly support the contracted service on-demand by the customer organization with appropriate data handling considerations.
None of this is unreasonable. Many of the requirements overlap with data protection regulations and cybersecurity frameworks already in place with numerous MSPs. Since these requirements are highly publicized, you must meet them to remain competitive in the market.
Turn These Recommendations into a Marketing Message
Imagine being able to show your best clients that you meet all the requirements for MSPs defined by the security agency responsible for protection of the United States.
Start with something like, “”The government warned you about outsourcing IT services. They are right, which is why we meet or exceed each of their recommendations.””
- Create a Shared Responsibility Model that looks something like this:
- Update your Managed Services Agreement (MSA) or Terms and Conditions to address each of the CISA contract recommendations.
- The Software Bill of Materials (SBOM) references a presidential Executive Order issued in May 2021, directing software vendors to create detailed records of the components used to build software, with the goal of tracking known or newly identified vulnerabilities. SBOMs are similar to the Material Safety Data Sheets (MSDS) that businesses like Home Depot must have available for all the chemical-based products they sell.
- Now that CISA has publicized its recommendation, you should formally request an SBOM from each of your software and cloud service vendors. Reference both the Executive Order and the CISA recommendations for outsourcing IT support. If a vendor refuses, you should talk with their executive team and consider selecting a more cooperative vendor if they won’t comply.
- Another way to improve your security is to implement the NIST Cybersecurity Framework (CSF) in your own company and use it as a base framework for your services. The NIST CSF is recognized internationally and provides protection against HIPAA audits and investigations, and provides an affirmative defense against lawsuits in several states.
- To validate your cybersecurity implementation and be seen as a cybersecurity authority, earn CompTIA’s Security Trustmark+, an audited business-level accreditation based on the NIST CSF. I have earned the trustmark for three of my own companies and have coached over 45 companies to earn it. Every MSP that has earned the trustmark has said the process helped them address security gaps and it gave them a tool to differentiate their MSP business from their competition. Bryan Hornung, founder of Xact IT Solutions, in Marlton, N.J., recently earned the CompTIA Security Trustmark Plus and soon after was interviewed by Forbes, CNN, and local TV news about ransomware attacks. Instant authority!
Don’t think of the CISA MSP warning as putting you on a known terrorist list. Instead, think of all the ways you can use it to be seen as a cybersecurity and compliance authority, build confidence in your company, and differentiate yourself from your competition.
MIKE SEMEL is a former MSP and founder of Semel Consulting and Semel Systems. Mike helps turn MSPs into cybersecurity and compliance authorities without taking the time to become an expert. His CompTIA Security Trustmark+ System has helped over 45 MSPs earn CompTIA’s Security Trustmark+ using his videos, templates, and personal coaching.