ANYONE IN THE BUSINESS of defending computer networks, which of course is all of us, knows that attackers have the advantage over the long run. To secure a network, we must secure every device and potential entry point, plus educate some challenging end users. The attackers need find only one entry point, or trick just one person. Addressing this requires both a tactical approach to security and the strategic application of carefully chosen solutions.
In this four-part series, we’ll look at strategic solutions for advanced security, the associated issues, and how Net Sciences manages each in turn. We will first cover vulnerability scanning and new device alerting here. Upcoming topics will include firewall log analysis and response services from a SOC or SIEM; providing simple, secure remote access without the exposure of open ports or the complexity of provisioning and supporting SSL VPN access; and managing in-place encryption for all devices.
Step 1: Looking for Holes
As we head into 2020, it is safe to assume that any competent MSP delivers on the basics— patching of Microsoft and other software, effective endpoint protection, and a solid unified threat management device providing defense of the gateway, preferably including content filtering. Most of us also deliver additional services such as DNS filtering (delivered both inside and outside the network by means of agent installs), user training and test phishing, and perhaps dark web monitoring as well. At Net Sciences, these are the features of our Basic Security Package that everyone gets.
But what aren’t we covering here? The answer is, quite a lot. First, we must find missing patches, deprecated protocols, and other such issues before bad actors do. New device alerting is great too. Let’s start here.
Step 2: Filling the Holes
I was looking for a way to “”check on our work”” by scanning for internal vulnerabilities and retired protocols. I was also looking into how to address issues related to IoT (Internet of Things, aka Internet of Threats) and realized that I wanted to go beyond isolating them by VLAN. I wanted to be alerted when new devices were added to our networks, but sought a kinder, gentler answer than angering clients by blocking new MAC addresses. Finally, I was hoping to find a way to discover default credentials on networked devices.
There was no shortage of options here, but each one was limited in scope, or by complexity or cost for SMB deployment. From solutions built into RMM tools to dedicated software tools such as Auvik, each seemed to be either too narrow in scope or not priced in a manner I could work with. Services such as those provided by Rapid7 and Tripwire were clearly too costly for smaller SMB deployments. Nothing covered all the bases and seemed to fit just right. Then I chanced across a little-known name in our space: Nodeware from Infinite Group.
Delivered as either a VM or a tiny Intel NUC-based appliance, Nodeware offers continuous internal vulnerability scanning services priced at a point that allowed us to deliver and package it very easily. Nodeware also finds default device credentials and alerts us to the addition of a new MAC on any monitored subnet. And as a final added benefit, you can schedule external vulnerability scans as well for external IPs of your choosing. These scans are no substitute for a true penetration test but are easier than running open source tools on your own.
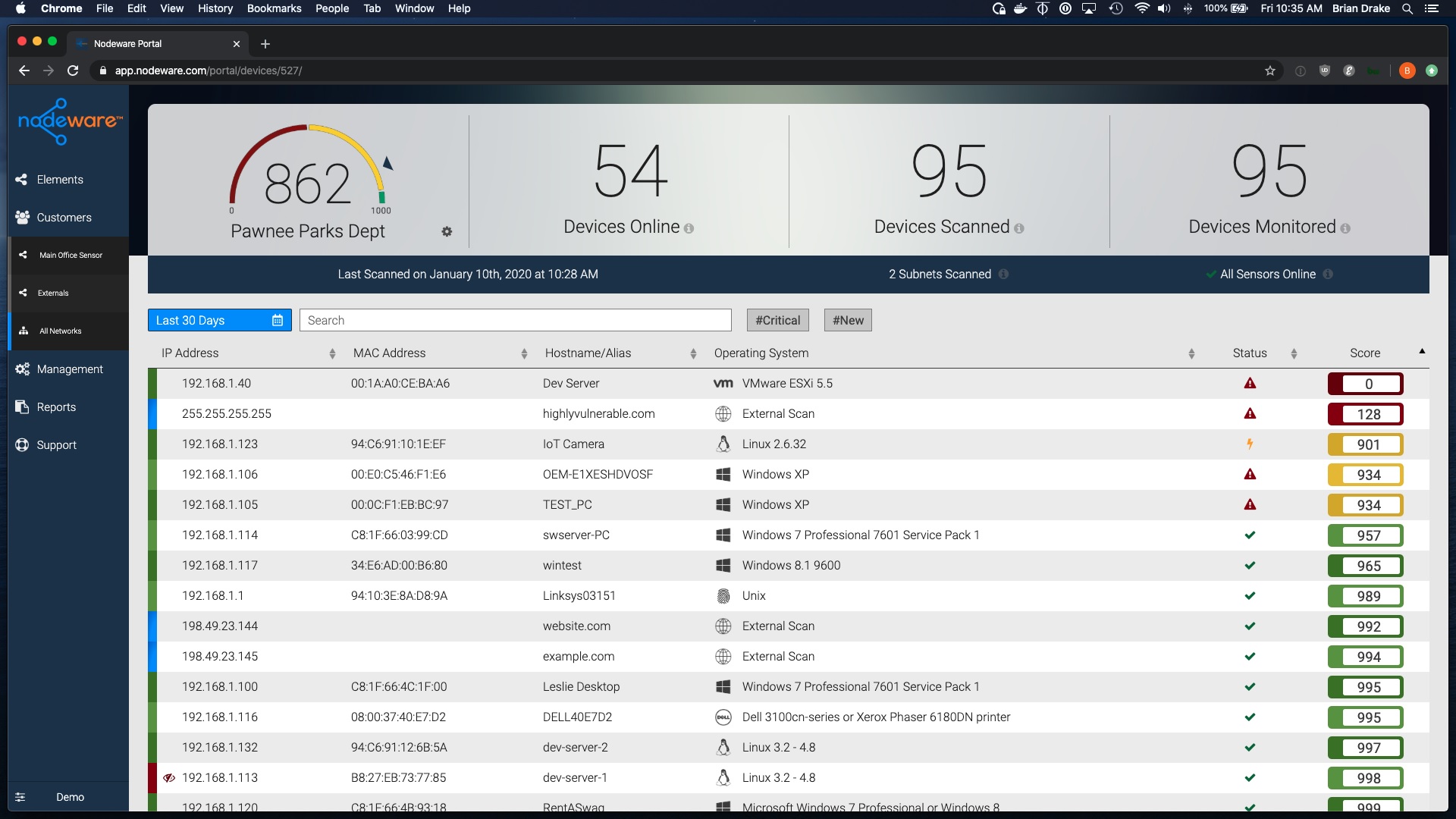
Another plus with Nodeware is the ease of deployment and its nice graphical interface. It presents an overall “”security posture”” with a score from zero to 999. You can drill down to any given device to see its reported deficiencies (indicated as low, medium, high, or critical risks). Then you can drill down further to see each potential vulnerability reported and suggested remediations, or in some cases just read up on why you can’t fix it (see below).
This might, for example, help you discover your networks are rife with self-signed certificates or older cypher suites, or missing AMT patches—all highly valuable information for anyone securing networks. But there are some challenges too. Many reported deficiencies (especially low-risk ones) are simply informational and cannot be patched. And there are still occasional errors in device or OS reporting. Keep in mind as well that each time you deploy these you will be creating work for your team, but it will be important work that will benefit you—and your customers—in the longer run.
Step 3: Selling This Solution
This solution has helped me present complex information in a graphical way that our clients can easily grasp. By showing them the device interface, as well as describing some of the issues it uncovers, I can “”put a face”” on some of these more abstract concepts for them. For example, with “”deprecated protocols”” I explain how ransomware encryption attacks can spread on networks still running Common Internet File System (aka SMBV1) and how important it is to remove that. And who doesn’t like seeing a nice dial with a 960 score on it?
As with any other type of selling, bundling is likely to be the way you want to deliver this service. At Net Sciences, I package Nodeware as two separate services: internal vulnerability scanning with new device alerting, and on-demand external vulnerability scans. The external scan lends itself to some wonderful storytelling, by the way; I still lean on the Bellagio hack through the fish tank thermometer for this. I bundle Nodeware with firewall log analysis and response (subject of the next article in this series) and offer them together as our Advanced Security Package.
Deployment 101
Setting up the appliance is easy. Set a LAN address on the device to match the subnet you’re monitoring. Then configure the device in your reseller portal and you’re there.
Nodeware is not without flaws, including its tendency to cross subnets if you have site-to-site VPNs in place, and some “”noise”” that you’ll need to turn down over time. You’ll also have to decide if you want to leave new device alerting on if you are monitoring a Wi-Fi subnet with frequent guests.
But with the ability to offer continuous internal vulnerability scanning, new device alerting, and on-demand external vulnerability scanning all in one device, you’ve just taken a great leap forward in your security offerings.
JOSHUA LIBERMAN is president of Net Sciences, founded in 1996. A 25-year ASCII Group member, former rock climber and martial artist, and lifelong photographer, Liberman has visited five continents and speaks many languages. He also writes and speaks in the IT field and raises Siberian Huskies with his wife Heidi, who calls him the Most Interesting Geek in the World.
Opening image: Courtesy of Infinite Group