If you’ve ever seen the movie Finding Nemo, you know the famous line, “”Fish are friends, not food.”” Well, in the email security world, phishers are certainly not friends—but they do try to make you think they are.
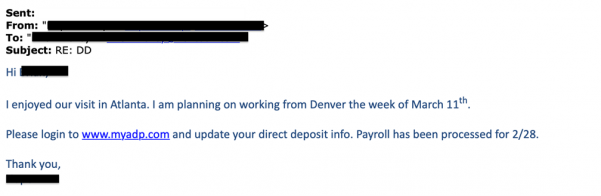
The new normal brought on by the COVID-19 pandemic and the shift to a remote work setting has made hackers evolve their phishing tactics even more. While you could normally detect a phishing email with a simple sweep for typos, fake logos, or other inauthentic items, phishers have found a way to outsmart even the most careful of individuals with reader-specific jargon that pertains to the user’s job position or other identifying marker—it is like they are using your own words against you.
To make matters worse, not only are hackers trying to pretend to be your friend, but they are doing so in a more structured way—and at scale. While it might be easy to spot that a phishing scam has hit an organization when all of the fake emails are identical, of late, phishers are taking a savvier approach. For example, instead of sending phishing emails in waves, with a single email hitting thousands of recipients, phishers are now crafting a single email to a specific target.
As a result, this creates more of a barrier for executives trying their best to combat phishing campaigns before it plagues their entire organization. In fact, each quarter, there are tens of thousands of unique phishing URLs detected and analyzed, proving especially detrimental to some channel partners that may not have the proper defenses in place for themselves and their SMB clients.
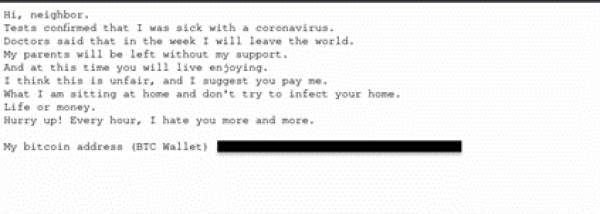
There is no doubt that cyberattacks are becoming increasingly sophisticated, and phishing scams are no exception. A key part of this shift is through social engineering attacks, which aim to do anything from pulling at recipients’ heartstrings, gaining their trust, or using events like COVID-19 paired with something in short supply, like vaccines, to spark a sense of urgency. For example, we recently identified a extortion email threatening to spread COVID to the recipient’s company and/or families if they refused to pay the sender.
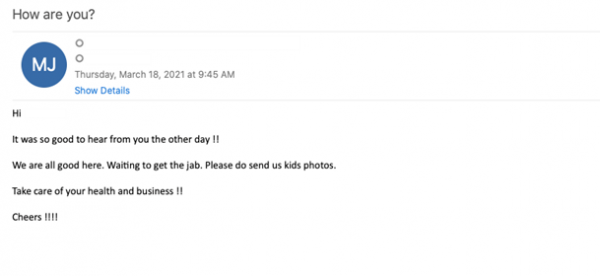
Another example of social engineering is catfishing, most seen on social media in the form of fake profiles used to gain the trust of unsuspecting users. The range of possibilities for social engineering attacks is endless, and end users are thus likelier to fall for the phish.
Extending beyond email, phishers are getting even craftier at creating fake Microsoft Office 365 login pages. These pages often have superior user experience and a better interface than the real login pages themselves, so much so that when individuals are asked to identify which one is legitimate, they often choose the wrong one.
With all of this in mind, what preventative measures should MSPs and channel partners take, and what should they do if they or their SMB clients fall victim? Here are a few key considerations:
- Caution your staff and your clients to remain wary of any emails that attempt to spark fear, uncertainty, or doubt, especially when they are tied to a current event.
- Do not rely on technology alone to protect against phishing attacks and instead look to a human-centric approach.
- Implement anti-phishing training for your clients and your own business that reflects the dynamic nature and latest trends of phishing emails. Deliver training on a continual basis and any time a user interacts with a phishing email.
- Ensure that a strong remediation plan is in place, including technology that can remove threats post-delivery, before users have a chance to click.
There is no silver bullet for preventing phishing attacks. However, by building a strong understanding of how to identify them and planning remediation beforehand in case things go awry is half the battle to weeding out phishers posing as friends.
ADRIEN GENDRE is chief product and services officer at Vade.