The Department of Defense is introducing a new level of scrutiny for MSPs, MSSPs, and security tool vendors that recognizes the critical role they play while securing defense contractors against cybersecurity threats.
If an MSP’s/MSSP’s defense contractor client is required to be assessed for Cybersecurity Maturity Model Certification (CMMC) Level 2 or 3, the proposed CMMC rule published on December 26, 2023, requires the MSP/MSSP to also pass an assessment at the same level. If the MSP/MSSP fails, the client fails as well.
Also in-scope for Level 2 and Level 3 assessments are cloud-based security solutions. The proposed rule includes many cost estimates – which are probably low, but you can see the significant cost of implementing NIST 800-171’s 110 controls and 320 assessment objectives at a level that will pass an audit, and then consistently [be compliant and pass audits] for years to come.
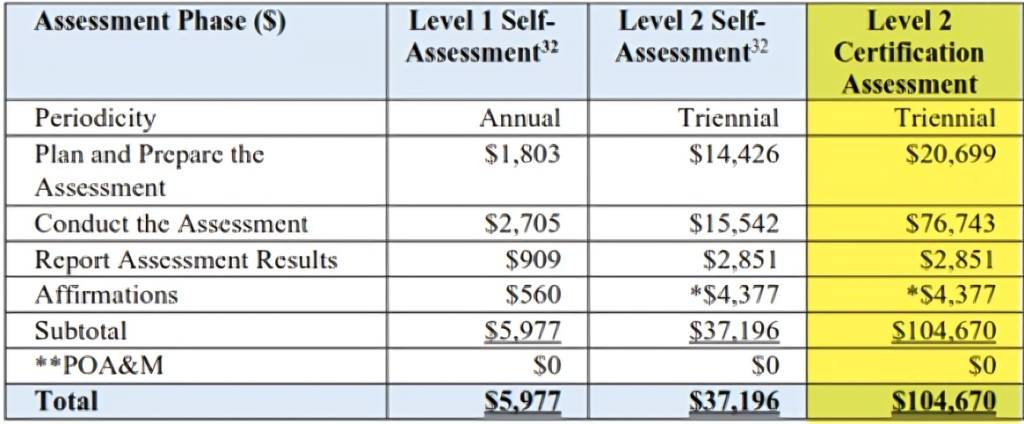
Source: CMMC Proposed Rule-Table 8
Level 2 assessments for defense contractors and their MSPs will cost $104,670 just to prepare and pass an assessment. The reason this estimate is low is that the assumption in the proposed rule states, “There are no nonrecurring or recurring engineering costs associated with a CMMC Level 2 Certification Assessment since it is assumed that the contractor or subcontractor has implemented NIST SP 800-171 rev. 2 security requirements.”
The assumption is based on the fact that implementing NIST SP 800-171 rev. 2 security requirements has been a requirement for defense contractors handling CUI since 2017. The $104,670 estimate doesn’t include the cost of implementing the controls, just preparing for the assessment.
For MSPs and companies that are new to the defense industry, the costs of implementing NIST 800-171 rev. 2 can easily be two to four times the cost of an assessment, or $200,000-plus.
The costs if your client must qualify at Level 3 are staggering:

Source: CMMC Proposed Rule-p. 115
As an MSP supporting defense contractors that qualify for a CMMC Level 3 assessment, you also need to be assessed at Level 3 at an estimated engineering cost of $2.7 million to prepare and $490,00 annually to maintain the security controls.
This obviously creates many challenges for MSPs.
- The NIST 800-171 r2 cybersecurity framework required by CMMC and the CMMC draft scoping and assessment guides, were not written while considering the types of services and tools used by MSPs/MSSPs, making third-party service providers and their security tool vendors difficult to assess.
- If a client will fail unless their MSP/MSSP has already passed an independent CMMC assessment, MSPs/MSSPs will need to be prioritized in the assessment schedules so they pass their assessment before their clients’ assessments.
- If an MSP/MSSP does not want to pay for an assessment and/or cannot afford the costs of added security at a level that will pass a CMMC assessment, they will no longer be able to support defense contractor clients that require assessments.
- How will the MSP/MSSP recoup the costs of complying? This may open the door for large, regional or national MSPs/MSSPs, who focus on defense contractors and can spread the cost of CMMC requirements across multiple locations, to displace local providers.
- While the CMMC program is focused on defense contractors, many of the increased third-party provider requirements are similar to what is being added to regulations in other industries (financial services, healthcare) and in business-to-business relationships between companies. If MSPs/MSSPs can pass a CMMC assessment, they will be able to use their certification for a competitive advantage in multiple industries.
- The cloud services in your security stack will need to be FedRAMP Authorized – which is expensive and time consuming – or be able to prove your security is equivalent to FedRAMP Moderate. A DoD memo defined FedRAMP Equivalency requirements and states that defense contractors are to take responsibility that all cloud service offerings (CSO) they use are compliant. Another requirement: The defense contractor is required to use cloud service vendors who commit to notifying them (cloud service vendor to MSP to defense contractor) if they are compromised in time for the end user to notify the DoD within the required 72-hour notification period from the time the incident was detected by the cloud service provider.
- Will the CMMC assessment ecosystem have the capacity to conduct all the estimated number of 82,000+ Level 2 and Level 3 assessments, not including any MSPs supporting defense contractors? The proposed rule says assessments will be phased in over a seven-year period but does not consider that prime contractors may encourage or require their subcontractors to receive certifications earlier so they are prepared just in case a new contract requires certification.
On December 26, 2023, the 234-page CMMC proposed rule for defense contractor cybersecurity was published in the U.S. Federal Register. In the accompanying scoping and assessment draft documents for defense contractors that access, store, or process controlled unclassified information (CUI), there are proposed requirements for MSPs and MSSPs to meet the same independently assessed 110 NIST 800-171 requirements as their clients.
The DoD refers to MSPs/MSSPs as external service providers (ESP) who provide services to defense contractors, which are identified as organizations seeking assessment (OSA). Cloud service providers (CSP) also are defined as ESPs in the scoping guides.
From the CMMC 2.1 Level 2 Scoping Guide (Draft): “If the OSA utilizes an ESP other than a CSP, the ESP must have a CMMC Level 2 Certification as set forth in 32 CFR § 170.19(c)(2).”
The security tools MSPs and MSSPs use to secure their clients are considered in-scope for a defense contractor’s assessment, along with the MSP’s/MSSP’s staff members. According to the CMMC 2.1 Level 2 Scoping Guide Draft:
- The “people” asset types are consultants who provide cybersecurity service, MSP personnel who implement system maintenance, and enterprise network administrators.
- The “technology” asset types are cloud-based security solutions, hosted virtual private network (VPN) services, and SIEM solutions.
- The “facilities” asset types are co-located data centers, security operations centers (SOCs), and OSA office buildings.
The proposed rule goes into effect after a 60-day public comment period that ends February 26, 2024, a DoD review of the comments, and a published final rule that may include changes based on the comments. This gives MSPs, MSSPs, and security tool vendors the opportunity to complain, criticize, or offer constructive suggestions on how the final rule should address ways that are affordable, achievable, and still meet the DoD’s goal to better protect our country’s warfighters by improving defense contractor data protection.

Mike Semel
This all may seem frustrating to MSPs, MSSPs, and security tool vendors. However, the CMMC was introduced and requires independent assessments of government contractors’ cybersecurity because the self-assessed cybersecurity requirements in government contracts since 2017 were largely ignored by the Defense Industrial Base that includes over 300,000 defense contractors.
Most defense contractors are small companies that subcontract portions of large defense contracts awarded to large companies known as prime contractors. The DoD will use the prime contractors to flow down the applicable CMMC requirements to their subcontractors. This means prime contractors will be putting pressure on their subcontractors to be ready to accept contracts that require CMMC.
Once CMMC is required in contracts – perhaps as soon as 2025 – a contractor that accesses, stores, or processes CUI will not qualify unless it has earned a certification through an independent assessment that will be good for three years. During that time, there will be annual attestations that the required cybersecurity is still in place. There will be a ramp-up period where some CMMC Level 2 contractors will be able to self-assess their compliance, and submit a score and a legal attestation to qualify for contracts.
There is an interim rule in effect that requires defense contractors with DFARS clause 204.252-7012 in their contracts to self-assess their compliance and post a score on a federal website to qualify for new contracts or current contract renewals.
Penalties will be severe. If an entity legally attests to its cybersecurity but does not consistently implement it, the DoD can ban the entity from further contracts and refer the contractor to the Department of Justice for civil penalties under the federal False Claims Act Cyber Fraud Initiative. That would require the contractor to pay back three times what it billed the government.
MSPs, MSSPs, and security tool vendors should take this opportunity to offer comments to influence the final rule.
Mike Semel, “The Complianceologist,” is president of Semel Consulting. He is a Certified CMMC Professional, CMMC Registered Practitioner, Certified Security Compliance Specialist, Certified HIPAA Security Professional, Certified Business Continuity Professional, and a Certified Cyber Resilience Professional.














