During an executive client briefing, I showed the CEO his organization’s written cybersecurity policy, which stated that all data must be stored on servers and was prohibited from being stored on local computers. Then I showed him their written policy that all data protected by regulations must be encrypted. Finally, I showed him reports from our “under the skin” network scans identifying protected data on unencrypted local PCs.
The CEO asked (with more than a little frustration), “Why aren’t our people following our policies?” I replied that I was about to ask him the same question.
It’s an important question to ask, given that three recent HIPAA penalties, each for more than $1 million, cited the failure to IMPLEMENT policies and procedures. And new Department of Defense requirements for defense contractors require proof that cybersecurity controls are being IMPLEMENTED OVER TIME.
Everyone just assumes that if they have a policy, people are properly trained and are following it. They usually find out the hard way—when something bad happens and their implementation is questioned by regulators or lawyers suing them—that they are wrong.
I’ve worked in my own business where I could implement a policy immediately. I’ve also worked for organizations where I needed multiple layers of approvals from executives and the boards, meaning that I needed to write policies that didn’t need to be revised and reapproved whenever something changed.
An easy way to understand how policies and procedures should be implemented is to understand what they are not.
• Cybersecurity policies aren’t procedures
• Procedures aren’t systems
• Systems aren’t training
What Is a Policy?
A policy is a brief, simple statement defining a rule that something is either required or prohibited.
If you must comply with multiple regulations, you can increase your chances of surviving an audit or investigation, or winning a lawsuit, by having separate policy manuals for the various regulations. This extra work pays off if you are audited for compliance, investigated after a data breach or other incident, or sued based on your alleged noncompliance with a regulation. By making it easy for an auditor to quickly see that your policies use the wording, and even the sequence, on which they base their audit, you increase your chances of success. Trying to combine multiple requirements into a single policy may seem easier, but will slow down and frustrate auditors, lowering your chances of success.
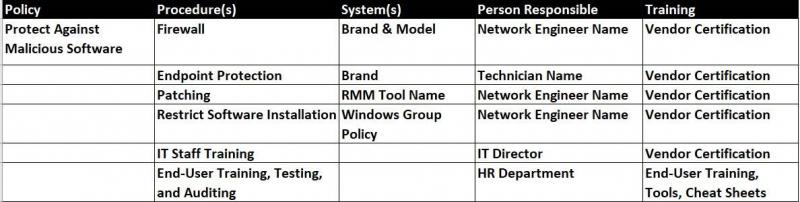
Policies should be vague, and not include details like procedures and systems, which are likely to change over time. For example, “We will protect our devices against malicious software. Our chief security officer will identify the procedures and systems to be utilized and will ensure all applicable workforce members have received the proper training.”
What Is a Procedure?
A procedure is a process that will be implemented to comply with a policy. Many times, it takes multiple processes to support compliance with a single policy.
For example, “To comply with our policy that we must protect our devices against malicious software, we will …”:
• Utilize a network firewall at the perimeter of our network that includes active intrusion detection and intrusion prevention (the standard for firewalls under HIPAA) and has the current firmware version installed
• Utilize automated services to protect against advanced persistent threats (APTs)
• Install endpoint protection (anti-virus/anti-malware) software on all computers and servers, and automate the update process to ensure current definitions
• Automatically install security patches and updates within 30 days of their release
• Automatically restrict the installation of software to privileged users
• Train our workforce to identify and avoid phishing email attacks
• Ensure our IT staff has current training or certifications in the cybersecurity tools we will implement
Note the multiple procedures to comply with just one policy. Also note that products, systems, and people are not named. By not including names, procedures don’t have to change unless you add another process.
What Is a System?
Think of systems as the specific tools—products and services—you will use to perform the process.
• Firewall = Brand and model
• APT protection = Name of online security service
• Endpoint protection = Brand and model
• Automated patches = RMM tool name
• List of security and product training and certifications
• Name(s) of end-user training tools
For each, you can also define general settings and the specific process and frequency that the systems will be checked to ensure they are implemented properly to support the procedures required to comply with the policies.
You can also identify individuals and their roles.
What Is Training?
Training is educating workforce members about what they should and shouldn’t do.
Some organizations mistake sharing policies with workforce members as a substitute for training. Policies are often written by lawyers and subject matter experts in a formal language that doesn’t always clearly answer the question, “What am I supposed to do?” or “What shouldn’t I do?”
 An example of a policy is the wording in the New York Vehicle and Traffic Law about stop signs:
An example of a policy is the wording in the New York Vehicle and Traffic Law about stop signs:
1172. Stop signs. (a) Except when directed to proceed by a police officer, every driver of a vehicle approaching a stop sign shall stop at a clearly marked stop line, but if none, then shall stop before entering the crosswalk on the near side of the intersection, or in the event there is no crosswalk, at the point nearest the intersecting roadway where the driver has a view of the approaching traffic on the intersecting roadway before entering the intersection and the right to proceed shall be subject to the provisions of section eleven hundred forty-two.
An example of training someone to comply with that policy/law is:
We require that you stop your vehicle when you come to an intersection displaying this type of sign facing you, and only proceed when it is safe to go:
By defining the simple required behavior, workforce members will not only understand what they must do, but recognize they can be disciplined for noncompliance. They don’t need to read the policy behind the training.
When it comes to training workforce members about cybersecurity, you need to use tools that make it interesting, simple to follow, and easy to implement. After training, use awareness tools like signage, monthly reminders, and cheat sheets to keep the information top-of-mind for consistency. Finally, test users periodically to ensure they know the procedures and audit them to ensure use.
For instance, when we do cybersecurity assessments we often work with organizations that have implemented email encryption to support their policy that protected information be encrypted when sent outside of the organization. During my “Security By Walking Around” site visits, I will ask the person escorting me which individuals are supposed to use email encryption. Then I will walk up to one, introduce myself, give the person my business card, and ask them to send an encrypted email to me.
More than half the time they fail. Why? Because they were trained once, sometimes years before, when the email encryption tool was implemented. Everyone just assumed that users would remember what information required encryption, how to use the encryption tool, and that it would magically happen every time.
What should happen instead is that after the initial training, users are given a cheat sheet so they don’t have to remember the multiple steps; they are tested periodically to ensure they know the steps (with no penalty for looking at the cheat sheet); and their Sent Mail folder is audited to ensure that protected information is always encrypted.
An easy way to manage the Policies/Procedures/Systems/Training process is with a simple spreadsheet:
Going back to the story about the executive frustrated with his staff for failing to comply with the policy to only store protected data on encrypted devices, if his staff managed the process using our simple spreadsheet they could have ensured consistent compliance.
Remember,
• Cybersecurity policies aren’t procedures
• Procedures aren’t systems
• Systems aren’t training
And, nothing happens magically.