ChannelPro 5 Minute Roundup for the Week of March 8th, 2021
This week, Erick and Rich have Datto’s big new security play on their minds, along with the power of sending unsolicited proposals to your clients and a new toy that proves it’s never too early to share the joys of work-from-home computing with your kids.
Datto Has Azure Continuity Solution Coming
The new product, which will provide disaster recovery for Azure-based workloads, fits within a larger “cyber resilience” strategy that also includes security offerings like the software Datto officially bought this week, according to CEO Tim Weller (pictured).
Barracuda Launches MSP Version of CloudGen Access and Updated, Renamed RMM Release
The new edition of Barracuda’s zero-trust network access solution features multitenant management and subscription pricing. The vendor’s RMM system, formerly named Managed Workplace, is now called Barracuda RMM.
Datto Acquires BitDam in Biggest Move Yet into Security Market
The threat detection vendor’s solution, which is designed to defend SaaS collaboration applications from ransomware, malware, and phishing, will be Datto’s first security-related product other than BDR offerings.
ChannelPro 5 Minute Roundup for the Week of March 1st, 2021
Erick and Rich explore Microsoft’s latest security upgrades and headaches, explain why MSPs should focus on profit rather than revenue, and present one more example of why uncaged animals simply don’t belong in passenger cabins.
The ChannelPro Network Hosts Business Management Online Summit
The live, full-day event focused on best practices in sales, marketing, operations, financials, and metrics for SMB technology providers.
How MSPs Can Maximize Revenue in the Face of Churn
Reducing risk, leveraging the cloud for agility, and providing (and proving) good value are just some ways to retain customers and prosper.
Arcserve Extends Sophos Security Integration and Nutanix Protection Features
Version 8.0 of the vendor’s Unified Data Protection solution adds integration with Sophos Intercept X to the product’s on-premises software edition, and lets users backup Nutanix Files, Nutanix Objects, and Oracle databases.
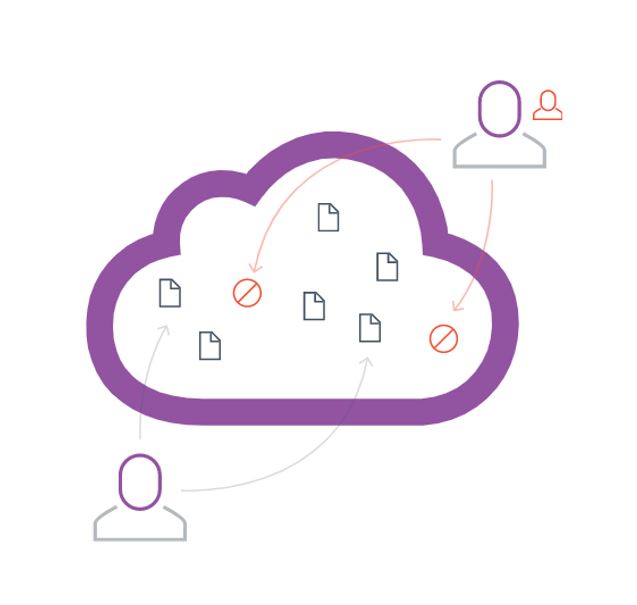
How Secure is Your Cloud Data?
With employees working remotely at higher rates, business data is increasingly at risk. While remote work and productivity rates are high, the same can’t be said about the security of cloud data that remote workers generate. Get statistics and more is this whitepaper on the data security challenges and gaps IT administrators still have to face.
Simply complete the form below to download the full white paper.
Voice of the (Socially Distanced) Vendor: Episode 14
Check in on the latest from Solutions Granted and Zomentum and meet a channel newcomer named Gradient MSP courtesy of your guide to all things vendor, Joel Zaidspiner.