Topic: Security - Page 188
Zix Acquires the Assets of Email Security Provider DeliverySlip
Acquisition Expands Company’s Product Suite and Customer Base, Delivers Cost Savings, and Creates Additional Cross-Selling Opportunities
SYNNEX Corporation Invests in Security, Networking and UCC Portfolio through Enhanced Platform, Expanded Offerings
Distributor continues to address digital transformation with new offerings for partners
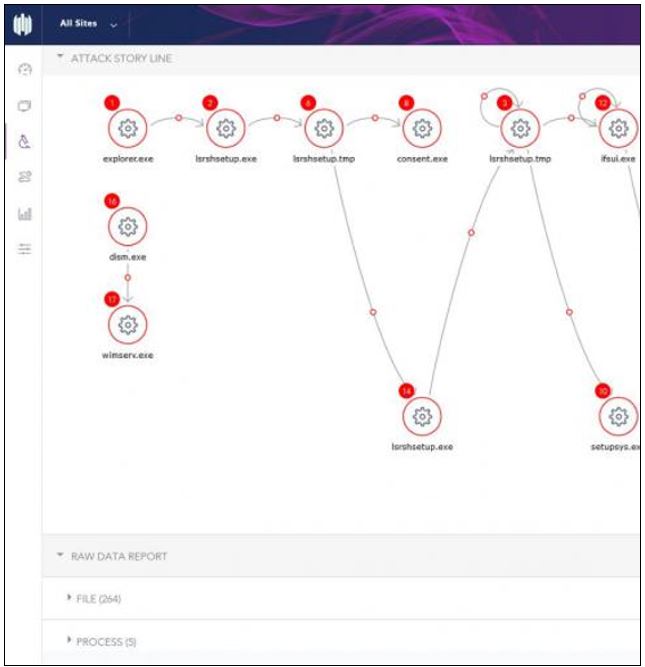
Cynet Announces Free Incident Response Tool to Validate, Understand and Remove Active IT Security Threats
Company Introduces IR Option with Unmatched Speed and Efficiency to Identify Live Threats in Compromised Environments
Nine-in-Ten Data Breaches in the Cloud Caused by Social Engineering, Finds Kaspersky Lab
SMB and enterprise IT leaders worry about data security practices at third-party cloud providers, but social engineering tactics are a bigger threat
Ponemon’s Third Annual Study on Third Party IoT Risk: Companies Don’t Know What They Don’t Know
Third Party Risk Factors Require More Board Level Attention on IoT Security
Tech Data Calls Security a Shared Responsibility
A new sales team, managed security service catalog, vendor incubation program, and training facility are key ways the distributor will fulfill its part of that bargain, according to security executive Alex Ryals (pictured).
Proofpoint Enters into Definitive Agreement to Acquire Meta Networks; Boosting Cloud Security Capabilities
Proofpoint’s cloud security offerings and adaptive controls further advanced with acquisition of an innovative zero trust network access platform and world-class R&D team in Tel Aviv
SolarWinds Ships Endpoint Detection and Response Solution in Partnership with SentinelOne
Equipped with patented artificial intelligence technology, the new offering aims to help MSPs better view and react to ongoing security threats.
ID Agent Builds Azure Active Directory Synchronization into its Security Training Solution
Available at no extra cost, the new functionality lets users of the vendor’s BullPhish ID product identify “targets” for awareness campaigns without manually uploading user lists, according to ID Agent exec Dan Tomaszewski (pictured).
Kaseya Introduces Turnkey Resources for Launching Security, Compliance, and Backup Practices
Called Powered Services 2.0, the “go-to-market-in-a-box” offerings are designed to help MSPs launch lucrative new services faster by sharing proven best practices from more experienced providers.