Topic: Hardware - Page 43
RapidFire Tools Adds Breach Detection to Cyber Hawk Internal Security Solution
Available in both free and advanced editions, the new functionality automatically searches for advanced persistent threats, keyloggers, malicious registry changes, and other intrusions that have gained a foothold on monitored end points.
ConnectWise Outlines Massive Managed Security Enablement Campaign
According to CEO Arnie Bellini (pictured), core elements of the initiative include the launch of an open source security integration standard and the introduction of new cybersecurity solutions, some of which will compete with products from ConnectWise partners.
Beachhead Rolls USB Security into Premium Edition of SimplySecure PC
Formerly available as a stand-alone product or add-on to any edition of Beachhead’s PC encryption and access management solution, SimplySecure USB is now exclusively available as a free, standard feature of SimplySecure PC Premium.
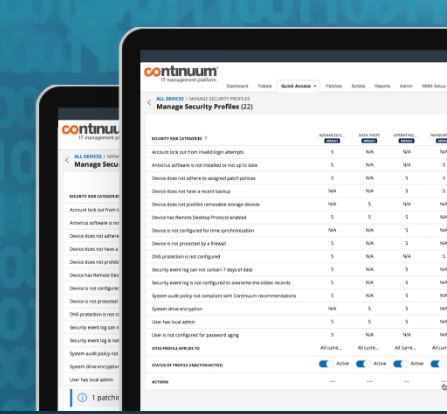
Continuum Adds Webroot DNS Security Software to Managed Security Platform
Under an expanded alliance agreement between the two vendors, Continuum partners can now purchase Webroot’s SecureAnywhere DNS Protection solution from inside Continuum’s RMM platform, and use the system at no extra cost.
Explosive IoT Growth Slowed by Early Adopter Paradox
Extensive multi-year F-Secure consumer survey finds the consumers most excited about connected home devices are also most aware of the privacy risks
ASCII Success Summit Wraps Up in Seattle with Awarding of ASCII Cup
At the final leg of the 2018 tour, MSPs, VARs, and other attendees spent two days in business building sessions then celebrated their picks for the best of the best at the ASCII Cup party.
Schneider Electric Launches Cloud Solution Resale Program
The power management vendor’s new APC Technology Partners Initiative lets channel pros offer unified threat management solutions from Untangle, BDR software from Infrascale, and 4G/LTE failover services from Accelerated Concepts Inc. at top-tier discounts.
ID Agent Integrates with Autotask PSA Solution
In the first of many integrations with widely used managed services tools coming soon, ID Agent’s dark web scanning service can now automatically create tickets in Autotask whenever it finds compromised user credentials.
Tech Data and Cisco Partner on Pre-Assembled Small Office Solutions
Called Branch Interconnect and Clinic Interconnect, the two new offerings combine networking, security, and collaboration products from Cisco with outsourced, white-labeled managed services from Tech Data.
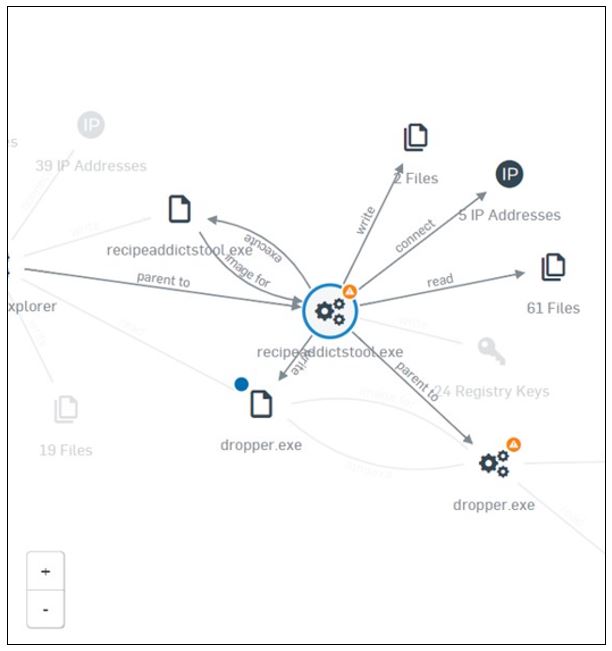
Sophos Adds EDR Functionality to Intercept X
Available now through an early access program, the new addition to the vendor’s next-generation endpoint security solution allows users to analyze suspicious files and get targeted advice on responding to them from the SophosLabs threat intelligence database.