US Signal Launches Vulnerability Management as a Service
The VMaaS offering comprises external, internal, and agent-based vulnerability scanners configured and managed by the data center service provider’s SOC team.
RMM Innovator Peter Sandiford Returns as CEO of Cloud Management Startup
Multi-cloud identity management vendor Zerotek is one of two SaaS administration companies founded by a pioneer of RMM software this year.
Regulation Comes to Managed Services
Louisiana became the first state to regulate MSPs. Will more follow?
ChannelPro SMB Forum Wraps Up 2020 with a Virtual West Coast Swing
ChannelPro’s final of five planned regional events offered a full day of content and networking geared at helping MSPs and IT solution providers continue to thrive in our new normal and prepare for emerging opportunities in the year ahead.
Security Dangers Present Risk and Reward for Partners, According to Tech Data
Security VP Alex Ryals discussed current and long-term threats, as well as technologies for mitigating them, during a keynote presentation at the company’s Security Enforce event today.
Tech Data Touts Benefits of Apollo Global Management Acquisition
Speaking at a virtual conference today, security exec Alex Ryals (pictured) said that investments from the private equity that now owns Tech Data are already helping streamline operational processes and consolidate disparate tools.
ChannelPro 5 Minute Roundup for the Week of October 26th, 2020
Erick and Rich dive into the new incident response service from Sophos, knowing when it’s time to pull the plug on a new business strategy, and some Halloween decorations in Dallas that may have taken the holiday spirit a touch too far.
Solving Edge Computing Infrastructure Challenges
Edge compute (distributed IT) installations have become increasingly business critical. Deploying and operating IT at the edge of the network, how-ever, comes with unique challenges. Solving them requires a departure from the traditional means of selecting, configuring, assembling, operating, and maintaining these systems. This paper describes a new, emerging model that involves an integrated ecosystem of cooperative partners, vendors, and end users.
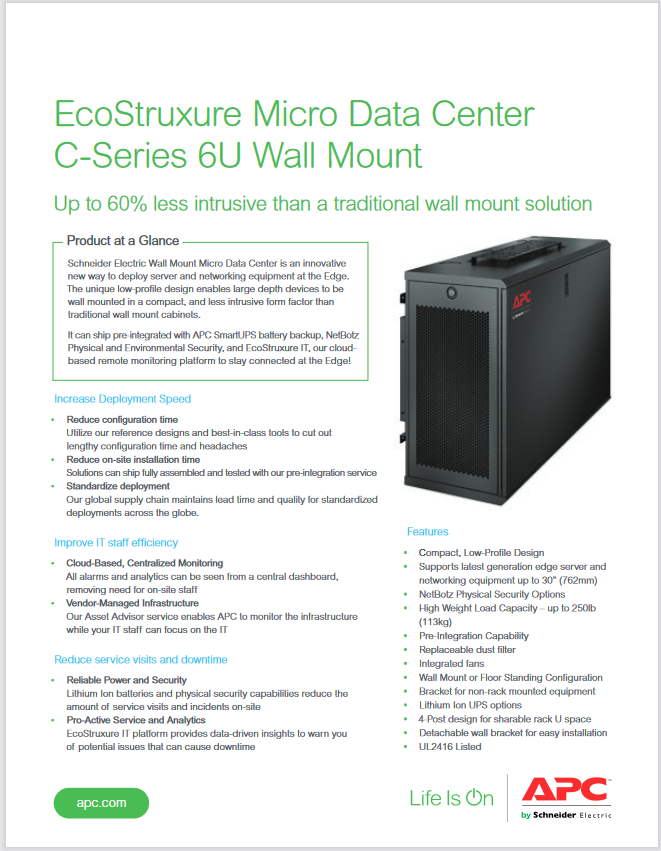
EcoStruxure Micro Data Center C-Series 6U Wall Mount
Schneider Electric Wall Mount Micro Data Center is an innovative new way to deploy server and networking equipment at the Edge. The unique low-profile design enables large depth devices to be wall mounted in a compact, and less intrusive form factor than traditional wall mount cabinets.It can ship pre-integrated with APC SmartUPS battery backup, NetBotz Physical and Environmental Security, and EcoStruxure IT, our cloud-based remote monitoring platform to stay connected at the Edge!
Cost Benefit Analysis of Edge Micro Data Center Deployments
Several IT trends including internet of things (IoT) and content distribution networks (CDN) are driving the need to reduce telecommunications latency and bandwidth costs. Distributing “micro” data centers closer to the points of utilization reduces the latency and costs from the cloud or other remote data centers. This distributed data center architecture also provides physical infrastructure benefits that apply to any small data center regardless of the latency requirement.