Topic: Hardware - Page 48
Conquering IoT Networking Challenges
Integrators need to factor in location of sensors, power, battery life, performance, and more when implementing IoT solutions.
ICYMI: Our Channel News Roundup for the Week of October 4th
VMworld news from VMware, the arrival of Windows 11, new security goodies from WatchGuard, Zyxel, and Kaspersky, plus the world luckiest lottery contestant are just a few of the stories we waited all the way until now to tell you about this week.
ChannelPro SMB Forum Heads South to Raleigh
The ChannelPro SMB Forum Mid-Atlantic gathered MSPs, IT consultants, VARs, and integrators to discuss business strategies and technology trends for a changing workplace.
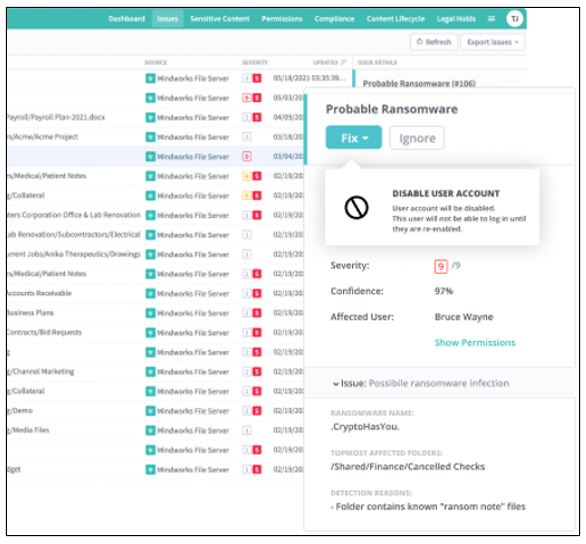
Egnyte Expands Ransomware Protection and Adds Ransomware Recovery
Subscribers to any of the vendor’s cloud file server offerings can now block ransomware attacks immediately. Enterprise subscribers can also inspect saved snapshots to determine when ransomware infected files and restore data to that point with one click.
ICYMI: Our Channel News Roundup for the Week of September 27th
Phone features for Teams, zero trust from Trend Micro, a new portable projector from Epson, and a furry, brown rodent whose portfolio is outperforming the S&P 500 are just a few of the stories we’ve finally managed to bring your way.
ICYMI: Our Channel News Roundup for the Week of September 20th
New Windows 11 devices from Microsoft and HP, a new partnership between Nutanix and Citrix, new email encryption capabilities from Zix, and what stands to be the world’s largest dog wedding are all among the stories we’ve finally gotten to.
Dell Enjoying Record Growth Despite Supply Chain Challenges
Though it’s enduring component shortages like everyone else, the technology giant believes the relationships and “buying leverage” it enjoys with suppliers give it a potential edge over smaller competitors.
ChannelPro Weekly Podcast: Episode #200 – Turning It Up to 11
Crank up the party music, people! Hard as it is to believe, ChannelPro Weekly has turned 200. Episodes, that is, and with them to celebrate with Matt and Rich is guest host Zac Cramer, of managed service provider IT Assurance. Together, the three of them discuss the new ticketing system from NinjaRMM, HP’s customer intelligence platform, and the decision at SaaS Alerts to sell a stake in the company to its MSP partners.
Zomentum Integrates MSP Sales Solution with Connect Booster
The new cross-platform link lets sales prospects targeted in Zomentum’s software accept quotes and complete purchases using credit cards or ACH via Connect Booster’s payments service.
HP Introduces Managed Print Program for Hybrid Work Environments
Currently being piloted, HP Managed Print Flex aims to help businesses with home and office workers adjust print outlays as business conditions in nonstop flux since the start of the coronavirus pandemic continue to change unpredictably.